In today’s digital landscape, businesses increasingly rely on software applications to manage operations, store sensitive data, and interact with clients. As cyber threats become more sophisticated and prevalent, the need for secure custom software has never been more critical. Custom software tailored to specific business needs can offer improved security features, which off-the-shelf solutions may need to improve. This article explores the significance of secure custom software, the risks businesses face, and how to mitigate these risks effectively.
Risks and Challenges in Secure Custom Software
The digital era has introduced numerous benefits but also brought several risks and challenges:
Cyber Threats: From malware, ransomware, and phishing to advanced persistent threats (APTs), cyber threats can compromise sensitive data and disrupt business operations.
Data Breaches: Unauthorized access to confidential information can result in financial loss, legal consequences, and harm to a company’s reputation.
Compliance Issues: Businesses must adhere to regulations such as GDPR, CCPA, and HIPAA, which require robust data protection measures to avoid hefty fines and legal troubles.
Evolving Threat Landscape: Cyber threats constantly evolve, challenging businesses to stay ahead of new vulnerabilities and attack vectors.
Benefits of Custom Software for Business Security
Custom software solutions provide numerous benefits compared to generic off-the-shelf applications, particularly regarding security.
Tailored Security Features: Custom software can be designed with specific security needs, incorporating features like encryption, access controls, and secure communication protocols.
Enhanced Data Protection: By addressing unique business requirements, custom solutions can better protect sensitive data and reduce the risk of breaches.
Improved Compliance: Custom software can be built to comply with industry-specific regulations and standards, ensuring that your business meets all necessary security and privacy requirements.
Flexibility and Scalability: Custom software can be adapted and scaled to meet new security challenges and requirements as your business grows and evolves.
Key Features of Secure Custom Software
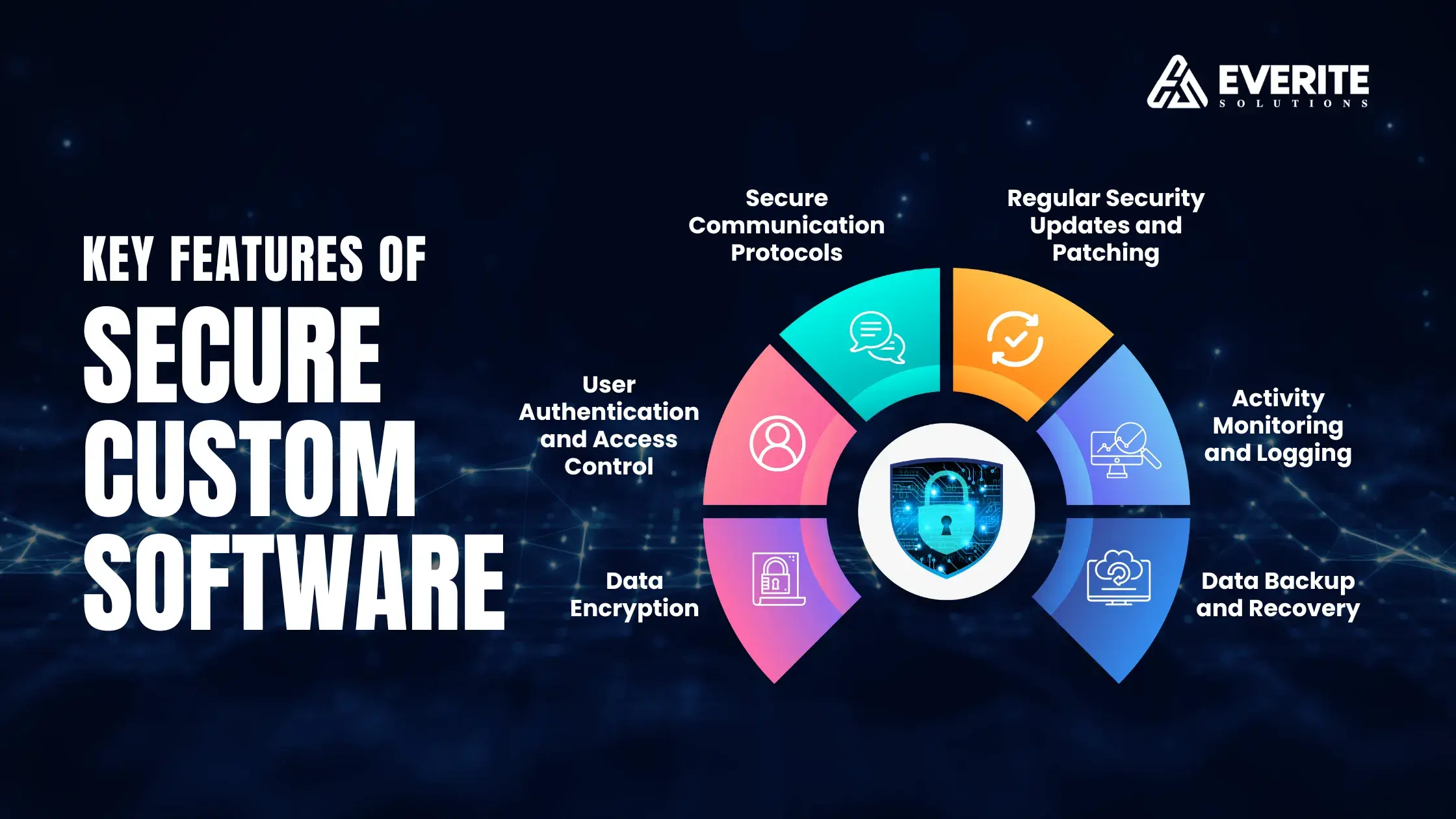
To ensure that custom software is secure, several key features should be incorporated:
Data Encryption:
Sensitive data is protected during transportation and storage by being converted into an unreadable format that can only be deciphered by authorized users.
User Authentication and Access Control: Only authorized individuals can access the software and its data. This includes multi-factor authentication (MFA) and role-based access controls.
Secure Communication Protocols: This protocol utilizes protocols such as HTTPS and SSL/TLS to secure data exchanges between the software and external systems.
Regular Security Updates and Patching: Keeping the software up to date with the latest security patches and updates to address known vulnerabilities.
Activity Monitoring and Logging: This system tracks and logs user activities to detect and respond to suspicious behavior or potential security incidents.
Implementing a Secure Software Development Lifecycle
A secure software development lifecycle (SDLC) is essential for creating robust and secure custom software.
Requirements Gathering: Identifying and documenting security requirements based on business needs, industry standards, and regulatory requirements.
Design and Architecture: Develop a secure architecture incorporating best practices and addressing potential threats.
Development: Follow secure coding practices to minimize vulnerabilities during the development phase.
Testing: Conduct rigorous security testing, including vulnerability assessments, penetration testing, and code reviews.
Deployment Strategy
Ensuring the software is deployed within a secure environment and that security configurations are accurately configured.
Maintenance and Monitoring: Continuously monitor the software for security issues, apply updates and patches, and perform regular security audits.
Preventing Cyber Threats with Custom Software
Custom software can play a significant role in preventing and mitigating cyber threats.”Customized software can effectively prevent and reduce cybersecurity threats.”
Customized Security Measures: Implement security features tailored to your business’s risks and requirements.
Proactive Threat Detection: Advanced threat detection technologies, such as intrusion detection systems (IDS) and security information and event management (SIEM) solutions, are used to identify and respond to potential threats in real-time.
Data Backup and Recovery: Ensure that regular backups are performed and that a robust data recovery plan is in place to minimize the impact of data loss or corruption.
Employee Training: Ensure that employees are well-versed in cybersecurity best practices, including identifying phishing attempts and adhering to strong password policies.
Choosing the Right Development Partner for Secure Software Solutions
Selecting a reputable development partner is crucial for ensuring the security of your custom software:
Proficiency and Background:
Choose a partner with a proven track record in developing secure software solutions and specialized knowledge within your industry.
Security Certifications: Ensure the development partner possesses relevant security certifications such as ISO 27001 or CMMI, demonstrating their dedication to security best practices.
Collaborative Approach: Ensure the partner collaborates closely with your team to understand your security requirements and business objectives.
Post-Deployment Support: Select a partner that provides ongoing support, including security updates, maintenance, and incident response.
Future Trends in Custom Software Security
Staying informed about emerging trends is essential for maintaining a robust security posture:
Artificial Intelligence (AI) and Machine Learning (ML) technologies are increasingly used for threat detection, automated response, and predictive security analytics.
Zero Trust Architecture: The Zero Trust model emphasizes never trusting and consistently verifying, which involves monitoring and validating all users and devices.
Enhanced Encryption Techniques: Advances in encryption technologies, such as quantum encryption, are expected to enhance data security further and protect against future threats.
Regulatory Changes: Stay updated on evolving regulations and standards to ensure your custom software complies with the latest data protection and privacy requirements.
Biometric authentication methods
The adoption of biometric authentication methods, such as fingerprint recognition, facial recognition, and iris scanning, is expected to become more widespread in custom software security. By incorporating biometric authentication into custom software solutions, organizations can significantly enhance user identity verification and access control mechanisms, reducing the reliance on traditional passwords and mitigating the risk of credential-based attacks.
Conclusion
Investing in secure custom software is a proactive measure that can significantly enhance your business’s cybersecurity posture. Addressing specific security needs, incorporating key features, and following best practices to “Safeguard your business from cyber threats and secure your sensitive data.” As the threat landscape evolves, staying informed about emerging trends and collaborating with experienced development partners to maintain a secure and resilient software environment is essential.
Visit our website, www.everitesolutions.com, to learn more about secure custom software. Contact us at info@everitesolutions.com or our mobile number, +1 404-835-1605, to schedule a consultation and discover how Everite can help shape your business’s future.


